Appcelerator Session Invalid Log in Again
Solving offline logout problem

A few days ago I had an interesting brainstorm with Chris Le Roy regarding offline logout process — the scenario when the user tries to log out but he is not connected to the internet. At first glance, it seems simple, but there few interesting bug related to security.
The content of this article can exist practical to both Android and iOs applications and even other clients that store session tokens.
Earlier we go there allow's consider login and online logout scenario to have a articulate picture of how our customer is dealing with authentication.
Login
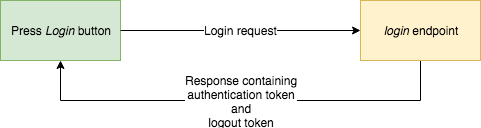
Nothing fancy here. Afterward the awarding starts user enters email and countersign, printing login push and awarding calls appropriate endpoint backed (server side) passing user credentials.

For security reasons, we don't want to store user credentials on the device because this would allow a potential aggressor to steal them in the time to come. That's why our hallmark request will simply transport credentials entered past the user and retrieve hallmark token that we will store on the device (instead of entered user credentials).
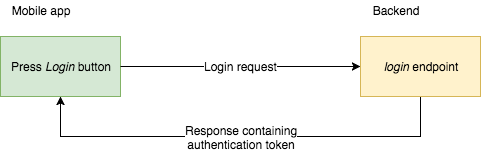
From now on each request our app brand to server volition require this token. The backend will check if the token is still valid and return data or acceptable mistake.
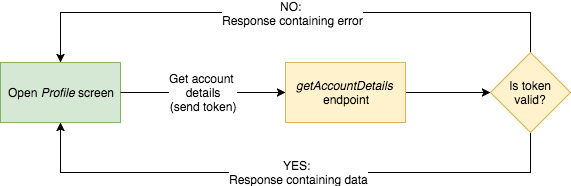
At backend this token is linked to a item user account, so each time we send or retrieve data server will exist operating in a context of that user e.thousand. calling getAccountDetails will return data for a specific user.
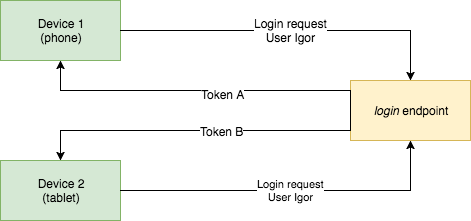
The token is also linked to particular device significant if a user will login twice from two dissimilar devices each device will retrieve dissimilar token.
To make our communication more secure we should consider implementation of certificate pinning (trust but certificates signed by certain document, non document authority that can be compromised)
Online logout
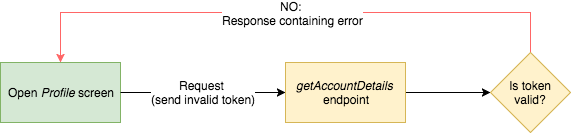
When application hits logout endpoint server volition invalidate the token and optionally perform additional operations similar unregistering device from Firebase (push notifications will not exist delivered to this device).
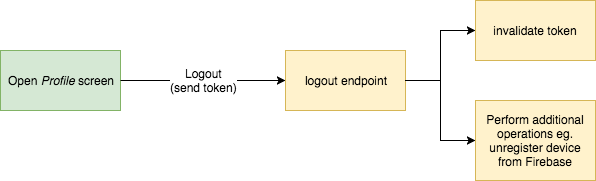
From this point, any other request using this token will fail considering session hallmark token (linked to a certain device) is not valid anymore.
Offline logout
Now we are getting to the tricky part. What should happen when user press logout button when he is offline? How our awarding should behave under the hood? Should we even testify logout button at all if there is no internet connectedness?

Let's get-go with showing or hiding logout button. Different applications solve this issue in different ways. Facebook awarding does indeed show logout push button, but Youtube developers decided not to do information technology. This behaviour is probably a result of very important difference betwixt those two application:
- Facebook explicitly asks user to login later on installing and launching the application, so explicit logout (showing logout button) is natural and associated action at the end of the catamenia.
- Youtube utilizes Google business relationship credentials that every user already have before installing application on the device (this account is required to access Google Playstore), then user never explicitly login into Youtube application.
Let's assume that our app is similar to Facebook — our user needs to explicitly login into our application. The easiest solution for offline log out would be to disable ability to logout when user is offline. However we want to improve security, then we want to allow ability to log out when app is offline. Permit's consider few options.
We could simply delete local hallmark token afterwards pressing logout button. Next time when user launches the app we verify that that token is non available on the device and we display login screen. Sounds practiced, only there are few issues with this solution. Commencement problem is potential security hazard (token at backend is still valid). Another problem are the notifications. About of the applications use some kind of push notification API (PubNub, Firebase , etc.). Commonly, backend registers the user device to receive push notifications. We need a manner to unregister the device, so user will not receive any more the notifications. In our instance, user would receive notifications even if he actually logged out, because backend wasn't notified about the logout.
As a fix for this problem nosotros might consider (Edit: ignoring notifications when token is not present on the device) or mark locally token every bit invalid, only exercise not really delete it. This potentially fixes our problem, considering when user launches the app nosotros would again display login screen and additionally perform logout request to a server. At commencement glance this may seems every bit good solution, simply at that place is a potential security risk here.
Let's presume we are using medical awarding, banking application or some other application containing sensitive data. Nosotros perform offline logout and infringe our phone or our phone is stolen. The attacker can copy all the application data and recall token (which is nonetheless valid on backend) and this volition allow him to hijack the associated session. Attacker to make a request using tool like Postman to recollect sensitive user data.
There are few other scenarios worth because:
- Our user does a fill-in of the app data using Titanium Backup (this backup app alone take 10–50M users) then logs out from the app — valid token still exists on the device.
- Our user was at the conference and used the public wifi network — attacker used Main in The middle assail to hijack his token. Latter user logged out from the app, but assailant even so have perfectly valid token
There is important lesson here — user assumes that there is no style to access account from this device because logout was performed properly, merely the device still stores valid token that allows accessing user personal, sensitive data.
Before nosotros endeavor to prepare information technology, allow's recap our goals. We desire to:
- remove token from the device in order to minimize possibility of launching attacks over hijacked sessions (minimize security take chances)
- have power to properly logout the user when the device is online in order to stop button notifications to exist delivered to the device and invalidate session token at server-side.
We could create endpoint working without hallmark token that volition allow unregistering the device using some unique identifier e.g. user email. However, that's is not platonic scenario because a malicious user could constantly disable accounts of other users forcing them to log in over again (unlikely but possible scenario).
The solution for our problem is introduction of 2nd token — logout token. Each fourth dimension our user logins he receives authentication token and logout token. Both tokens are stored on the device.
Logout token would be valid only for single usage and only for logout endpoint call.
At present when our user is offline and clicks logout nosotros delete authentication token (disabling ability to retrieve sensitive data) and leave logout token and then user tin can still log out properly. Nosotros should schedule a Job that will be executed later and that will endeavour to perform logout using logout token.
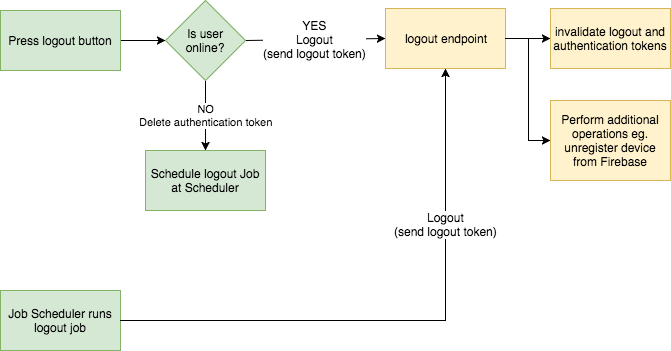
This way nosotros will exist able to log out the user properly and diminish security take chances.
K eep in listen that in that location may notwithstanding be the cases where logout token will never be sent eastward.g. user loses or destroys his telephone. That why token should be linked to some kind of expiration date (Accented/Idle/Renewal Timeout) e.one thousand. the token isn't used for 4 hours and then it is invalidated.
We should too consider implementing renewal token timeout just to keep our users safety in some scenarios similar erstwhile token hijack from public wifi.
Decision
Offline logout is not difficult to handle, but as yous can meet it requires a little bit of effort to brand it right and secure. I hope this article fabricated this procedure much easier to understand in terms of tradeoffs and potential security risks.
Special thanks become to Chris Le Roy, an Android security skillful.
Source: https://medium.com/android-news/solving-offline-logout-problem-f3b50da49e7e
0 Response to "Appcelerator Session Invalid Log in Again"
Post a Comment